What Does a Secure Web Connection Actually Do?
When surfing the web, you want to keep your personal information private, not leaving it open to be spied on by Internet Service Providers or other people on your network. For this purpose, an increasing number of websites and services are using secure web connections, shown by a padlock or similar indication in your browser's address bar. Such websites use "https://" at the beginning of their address rather than "http://". Think of it as automatic encryption. But what protection does that give you? How much of your surfing data is secure?
To find out, I'm going to use packet analyzing software to spy on myself as I browse the web and see what information is visible. Such software makes it possible to capture and examine traffic on a network, seeing the raw data that is sent between devices. The software I'm using is called Wireshark, which is free and open source, but there are many other similar tools available. The following is a crude test but I hope to show what that little padlock means in most circumstances.
General content
First, let's look at the content of a basic web page. The standard example website used by many tutorials is example.com which helpfully has both an encrypted (secure) and unencrypted version. The content is simply a short message and a link saying "More information." In Wireshark I searched for the word "information" and this is the result:
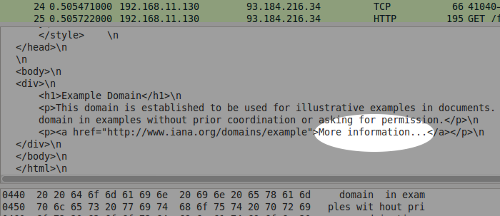
As you can see, it found the word "information" together with the rest of the page's content. In other words, everything I can see in the browser is also easily visible to anyone sharing my network or spying on my connection.
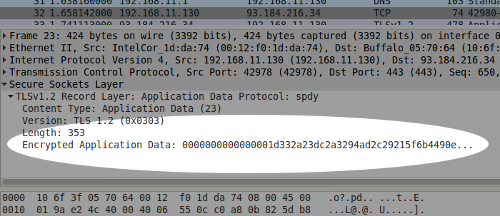
With the secure version, however, the content is encrypted and although Wireshark shows lots of packets of data, it's not clear what they contain.
Domains
Now we've seen the effect of a secure connection, let's see what other information it hides starting with the most fundamental — the domain name. This is the part of the web address (URL) that ends in .com, .org or similar. I'm switching websites this time and capturing data packets when I visit duckduckgo.com which is secure by default — we can tell by the "https://" at the beginning of the address. Looking at Wireshark's results, I quickly find a data packet containing the domain name, as you can see:
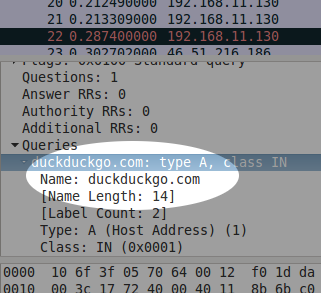
It may be surprising that the domain name is clearly visible but not only is it normal, it's essential. Without it, your router and Internet servers beyond wouldn't know where to send your requests for web pages. It's a bit like the luggage tag that's put on your suitcase when you check in at an airport — it needs to be visible for the various staff to send it to the right city.
Sub-domains
Sub-domains are areas within a domain. If we stick with the airport analogy, they're the equivalent of having one or more airports within a city. Consequently sub-domain names, for example safe.duckduckgo.com, are also visible within data packets even over a secure connection.
Individual pages
This is where things get reassuring. Like your luggage when it arrives at an airport, there's no need for its subsequent precise destination to be public. In the case of data packets, only the server at the destination domain (or sub-domain) should be able to decrypt the precise destination and so directory and page names are therefore not visible to external observers. This includes other parameters in the address such as ?query=keyword#target.
Form data
Finally, what about web forms which are often used for sensitive personal data? Sometimes this is sent as part of a web page's address, in which case we now know it's safely encrypted. Many times it's not however, and is sent by the browser passing on your information in the background. Fortunately this is treated similar to other content and encrypted when a secure connection is used. In fact when checking data packets I was not even able to tell what was form data, what was a page name and what was regular content. This is how it should be when data is encrypted.
Being careful
So as you can see, it's simple to summarize what data is protected when using a secure web connection:
- Domain and sub-domain in the URL: Unencrypted, i.e. visible
- Remainder of the URL: Encrypted, i.e. hidden
- All other page and form data: Encrypted, i.e. hidden
You may think you don't need such protection and that Internet spying only happens on a large scale or to high-profile people, but in fact when you're in a cafe, hotel, workplace or even in your own home, it's still possible for someone to monitor your data as shown in this experiment. Using secure web connections is an easy way to increase your privacy.
Unfortunately you can only use a secure web connection with websites that support it. DuckDuckGo search is secure by default of course, but there are many websites that aren't. However, we've released a desktop and mobile browser that will make sure encryption is used when available (in addition to other privacy features). It works in the background, silently redirecting you to secure connections when it can. We recommend installing it for your regular mobile and desktop web browsing, as well as keeping an eye on the address bar to look out for that padlock.
For more privacy advice, follow us on Twitter & get our privacy newsletter.
