What Do Security Certificates Actually Do?
In a previous post we saw the effect of encryption, trying to make content unreadable to anyone watching your traffic. Great, you may think, my DuckDuckGo searches are safe! Yes, but only if it's really DuckDuckGo at the other end of your connection. There are two parts to sending information securely over the Internet, whether it's private messaging, private web browsing or any other private data transfer, and encryption is only half the story.
- Encryption: Encoding the information so that it can't be read by anyone without the correct key.
- Identity verification: Verifying that the person or thing at the other end of the connection is really who they say they are.
Security certificates play a vital role in this verification and you may have seen warning messages in your browser about certificates being out of date or somehow incorrect. Let's look at how these certificates are used so you can hopefully have more trust in your online interactions and make informed choices when warnings appear.
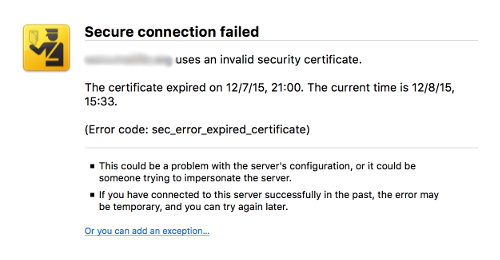
What is a certificate and who checks it?
Like everything on your computer or device, certificates are just files containing data. They're relatively small and contain details such as their date of issue and expiry, what domain they're valid for, who issued them and a supposedly unique, unfakeable "signature" made of letters and numbers called a hash*.
In some ways a security certificate is like a passport for a website — it verifies its identity — but you can't be expected to examine the certificate of every server (computer) on the web so, thankfully, your browser does that for you in the background. It's like your own personal passport control official. Every website you try to securely connect to has to present its certificate to your browser which makes various checks. If something's wrong such as the certificate being expired, its domain name not matching the one you're trying to access, or an incorrect signature, your browser will either show you a warning or simply block the site completely. As you can see, we place incredible trust in the browsers we use everyday but how do they know who to trust?
Who issues the security certificates?
Browsers can't be expected to know about every certificate on the Internet so instead they rely on core Certification Authorities (CA) — organizations that are verified by browser vendors. All browsers contain a list of certificates issued by trusted CAs called root certificates and they're the foundation of a chain of trust consisting of further certificates. Similar to a national passport issuing authority, the certificate issuers should make proper checks to verify the details of the people or organization controlling the website requesting a security certificate. The security of the Internet relies on this chain of trust and there are serious consequences if it's ever at risk, as was seen in April 2015 when a major root certificate authority was removed from browsers after the discovery of a rogue certificate. Incidentally it is possible to make your own "self-signed" certificate, just as it's possible to create your own passport, but it won't be officially recognized.
Isn't it possible to spoof the certificates?
Certificates rely on various things to be secure and trustworthy — the strength of the algorithm to create the signature and the competence of the issuing authority, for example. These naturally improve over time as knowledge and research findings spread, just as weaknesses in older methods appear. There have been cases of certificate spoofing and there may be again, but the likelihood is ever-decreasing.
So certificates make everything OK?
They're a great technology and work well. The fact that most people don't know of their existence despite using them every day shows how elegantly the system works. However, as long as there are systems to protect us there are people trying to defeat that protection. In the case of security certificates, there have been instances of ISPs, workplaces and even computers and tablets intercepting secure Internet connections using their own certificates. Instead of a single secure connection to your bank, for example, there might be a secure connection to your ISP and then a separate secure connection to your bank. Technically it seems secure but actually traffic is intercepted presumably without the user's knowledge. Fortunately the security community is full of helpful experts who look out for such untrustworthy behavior and spread the news quickly so it can be fixed (or avoided). It's also possible to check certificates yourself if you get suspicious.
How can I check certificates myself?
Usually within your browser you can click on the small padlock image next to the address bar, which only appears for secure sites, i.e. those beginning with https://. Then there should be a button to open the details of the certificate for you to view. Make a point of checking who the issuing authority is, what domain it's for (hopefully the one you're visiting!), when the expiry date is, and so on.

So with your newly-acquired certificate skills, what should you do? Well, nothing really. Continue to use the Internet as you normally do, albeit with hopefully a better understanding of the technology in place to protect you. If you do come across a certificate warning, however, now you should be able to investigate and decide for yourself how best to proceed. It may be a simple blog with a certificate that expired yesterday, or it may be a suspicious domain that's masquerading as your bank. Either way, it's good practice to let the website owners know and do your bit to keep everyone safer on the Internet.
Recommended reading: What is SSL and what are Certificates?
* A hash is created from some content in a one-way process so that any change to the content would generate a different hash. For example, imagine burning a printed document and closely examining the remaining ashes. If you edited, re-printed and burnt the document again the chemical composition of the resulting ashes would be (ever-so-slightly) different. It's also impossible to discover the content of the document just by examining the ashes, which is the same as with a hash.
For more privacy advice, follow us on Twitter & get our privacy crash course.
